Nemertes Research, a think-tank that specializes in analyzing and quantifying the business value of emerging technologies, recently developed a four-point scale that ranks an organization’s ability to detect, understand and contain cybersecurity breaches effectively. The four-level cybersecurity maturity model categorizes organizations based on the time it takes to detect a potentially dangerous occurrence, determine whether it represents a breach; and, if it does, contain the breach.
The model, loosely based on the U.S. National Institute of Standards and Technology (NIST) cybersecurity framework, assesses an organization’s security posture across several key areas including; organizational structure, policies and processes, and the technologies they employ. Based on the assessment, organizations are slotted into one of the four maturity levels.
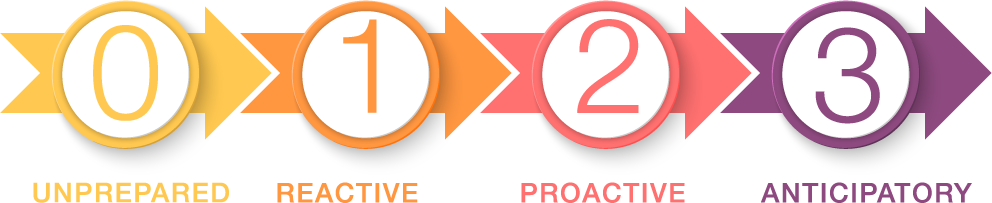
- 0 | Unprepared: Your organization lacks the necessary information to take action, rendering you unaware or unable to respond to current or emerging issues.
- 1 | Reactive: Your organization has the basic platforms and structures in place to react to business requirements but lacks the ability to proactively prevent problems from arising.
- 2 | Proactive: Your organization has the platforms and structures in place to proactively address issues and challenges.
- 3 | Anticipatory: Your organization has the platforms and structures in place to proactively address future issues and challenges.
Need help developing effective cybersecurity breach containment and mitigation strategies? A Cerium Networks Security Assessment can help you determine where your organization is on the cybersecurity maturity spectrum. Our knowledgeable consultants can help you develop a cybersecurity roadmap that will guide your organization to the next level.





