Most organizations grow and evolve their computer systems over time. They acquire and deploy new hardware and software solutions, bolting a variety of security solutions onto disparate systems along the way. With cybercrime on the rise, threats getting more sophisticated, and attack surfaces growing, ad-hoc legacy protection strategies and technologies are struggling to keep pace.
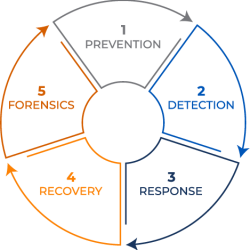
Effective defense for overcoming the challenges of advanced threats requires a comprehensive, integrated approach that includes five components cybersecurity and data protection. These components must be integrated, coordinated, and executed simultaneously to efficiently safeguard the confidentiality of your data and ensure the integrity and availability of your systems. Developing a comprehensive plan covering all five components forms a solid foundation for a successful cybersecurity and data protection program:
Effective defense for overcoming the challenges of advanced threats requires a comprehensive, integrated approach that includes five components cybersecurity and data protection. These components must be integrated, coordinated, and executed simultaneously to efficiently safeguard the confidentiality of your data and ensure the integrity and availability of your systems. Developing a comprehensive plan covering all five components forms a solid foundation for a successful cybersecurity and data protection program:
- 1. Prevention: Proactively stop threats at the perimeter before they breach your systems
- 2. Detection: Identify potential threats before they pose a risk to your environment
- 3. Response: Mitigate and reduce the impact of cyberattacks
- 4. Recovery: Restore compromised systems and data quickly and safely
- 5. Forensics: Investigate and analyze the root causes of threats
Effectively managing all of your security solutions, such as firewalls, data loss prevention, cloud access security brokers, endpoint protection, web app servers, etc., to address all five components can be a challenge. On top of that, continuously monitoring devices, services, and system layers, investigating and responding to alarms, patching and updating your systems, and backing up your critical assets can be overwhelming.
If you need help modernizing your cybersecurity capabilities, Cerium Networks can help. We have deep industry experience designing and implementing an array of security strategies, such as SD-WAN, software-defined perimeter (SDP), and zero trust network access (ZTNA), covering all five components of cybersecurity and data protection. We offer a wide range of industry-leading security solutions with advanced support and proactive managed services options for freeing up IT resources and improving your security posture.
If you need help modernizing your cybersecurity capabilities, Cerium Networks can help. We have deep industry experience designing and implementing an array of security strategies, such as SD-WAN, software-defined perimeter (SDP), and zero trust network access (ZTNA), covering all five components of cybersecurity and data protection. We offer a wide range of industry-leading security solutions with advanced support and proactive managed services options for freeing up IT resources and improving your security posture.
Supporting Your Cybersecurity Journey
With a broad portfolio and extensive expertise, Cerium Networks can help you cut through complexity to strengthen and streamline your defenses against cyber threats. Protect your organization from costly data breaches with a cohesive approach to cybersecurity aligned with your business objectives.





