“Darcula” represents a new breed of Phishing-as-a-Service (PaaS) posing a serious threat to both Apple and Android users. This sophisticated attack leverages encrypted text messages to disseminate phishing attempts in large numbers, with a primary focus on compromising user credentials. Darcula is capable of spoofing sign-in pages from over 20,000 different domains, with prominent entities like USPS being among the targets. What sets Darcula apart is its utilization of RCS protocol for Google Messages and iMessage, bypassing traditional SMS limitations. This allows attackers to embed phishing URLs directly into messages, exploiting the end-to-end encryption of RCS and iMessage, making it exceedingly difficult to intercept or block these malicious communications.
How it Looks
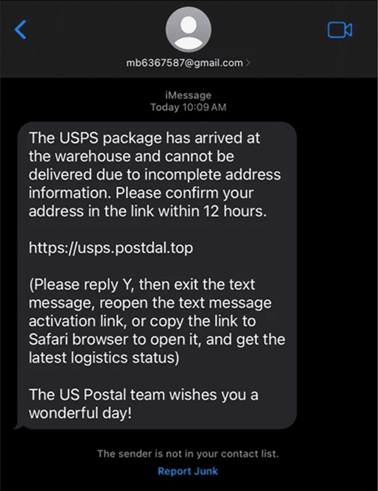
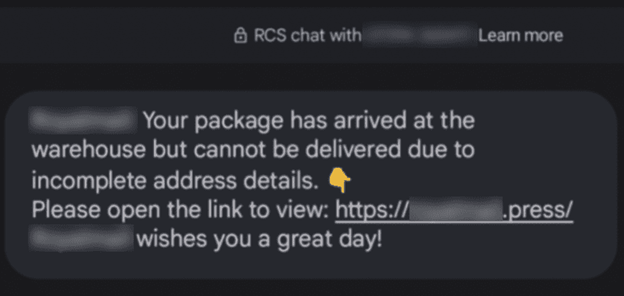
To combat Darcula effectively, user awareness training is paramount. Users must be educated on recognizing phishing red flags, such as unsolicited messages asking for urgent action, spelling errors, or enticing offers. It is crucial to instill a mindset of skepticism towards unexpected messages, especially those containing links from unknown senders.
Remember, the success of these attacks’ hinges on user interaction. By refraining from clicking on suspicious links and promptly reporting phishing attempts, individuals can play a pivotal role in mitigating the threat posed by Darcula and similar phishing campaigns.




